Sponsored by Fortinet
Sponsored by Appgate
The 2023 Faces of Fraud Research Survey Results Report
Sponsored by CyberArk
Critical Gaps in Securing Identities: 2023 Survey Results
Sponsored by CyberArk
Endpoint Security Challenges in Manufacturing - 2023 Survey Results
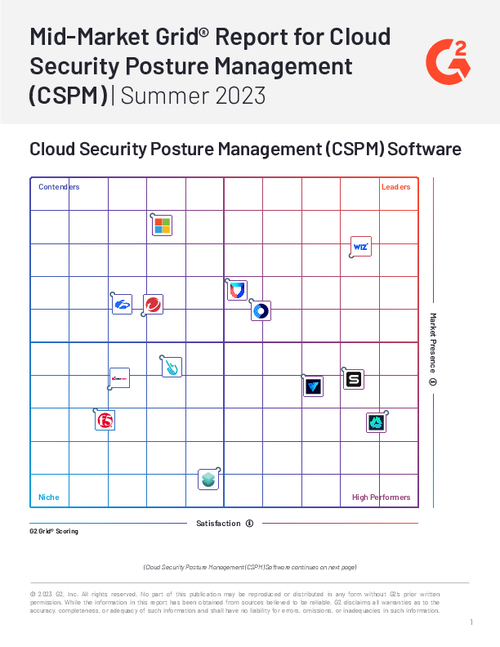
Sponsored by Wiz
Mid-Market Grid® Report for Cloud Security Posture Management (CSPM)
Sponsored by Wiz
AWS Security Foundations: For Dummies
Sponsored by Wiz
Security Assessment Sample Report
Sponsored by OneSpan
Banking Use Case Catalog
Sponsored by Proofpoint
Executive Research Report: 2023 Security Awareness Study
Sponsored by Saviynt
Three Steps to Application Access Governance Maturity
Sponsored by Sonatype
Perception vs Reality: Software Supply Chain Maturity
Sponsored by SecureLink
The State of Cybersecurity and Third-Party Remote Access Risk
Sponsored by SecureLink